User Access Intelligence
Detect and resolve critical data access vulnerabilities, at scale.
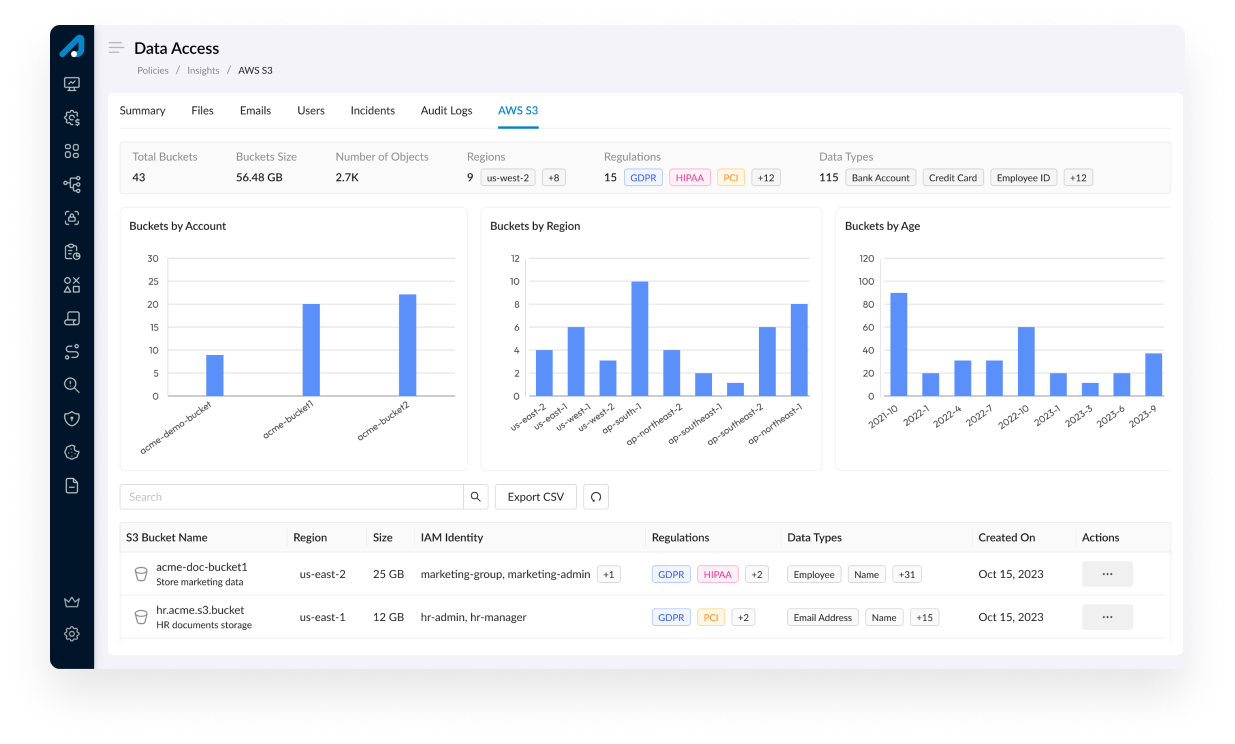
Data security with Zero Trust principles
Harness the power of Secuvy’s User Intelligence to discover applications, understand user interactions, and secure your digital infrastructure seamlessly.
Identify and mitigate overexposed user access and excessive data privileges to safeguard sensitive information from unauthorized access. Achieve Zero Trust by gaining a deep understanding of both user behaviors and the data that requires protection, guiding you toward a least privilege security model.
Detect, prioritize, and take action on vulnerable sensitive or critical data that may be at risk. Gain comprehensive visibility to support risk mitigation efforts, ensuring compliance with regulatory demands that necessitate extensive open-access controls.
Identify user groups with access to sensitive, critical, or high-risk data across your environment. Minimize overexposure and excessive user privileges to lower the risk of a potential data breach.
Automatically address and revoke unauthorized file access for users or groups. Remediate directly by assigning the task to the appropriate team member.
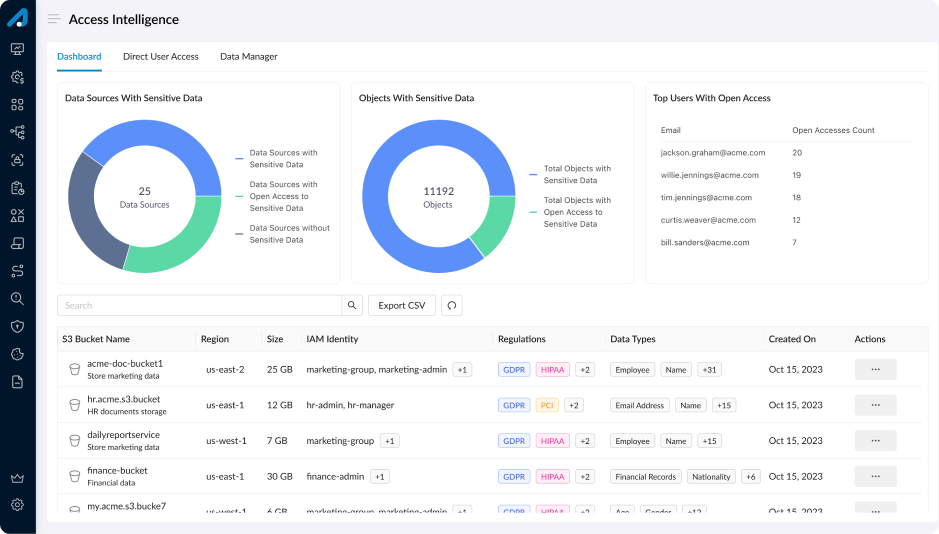
Transforming Access Intelligence
Secuvy’s Secuvy Platform, powered by self-learning AI, provides a centralized data view. It empowers you to craft comprehensive access assessments, ensuring the management, correlation, and protection of data access insights for privacy rights for compliance.
AI-Driven Access Insights
Leverage machine learning to gain deeper visibility into data access patterns. Uncover hidden risks, automate permissions management, and ensure that access is aligned with your security policies, all powered by intelligent, adaptive algorithms.
Identify and Investigate Access Issues
Quickly detect and analyze potential access concerns, ensuring your data remains secure and compliant.
Generate Comprehensive Audit Reports
Efficiently produce detailed audit reports to maintain transparency and demonstrate compliance with regulatory standards.
Resolve Access Violations
Swiftly address and correct unauthorized access incidents to maintain the integrity of your data security.
Filter by Open Access
Easily identify and manage data with open access, ensuring that only the right users have the appropriate permissions.
Internal and External Access Views
Gain complete visibility into both internal and external access to your data, empowering you to monitor and manage data interactions effectively.
Customize Access Permissions
Tailor access controls to meet the specific needs of your organization, ensuring the right people have the right level of access.
Unified Access Management
Centralize the management of access rights across your organization, streamlining processes and enhancing security oversight.
Secuvy Solution Brief
Benefits
Enhanced Security
Detect and mitigate unauthorized access, ensuring that only the right users have access to the right applications and data.
Improved Compliance
Maintain regulatory compliance with detailed records of user activities and access patterns.
Resource Optimization
Allocate resources more effectively by understanding application usage trends and user needs.
Streamlined Management
Simplify user and application management through automatic grouping and detailed monitoring.
Actionable Insights
Make informed decisions with comprehensive data on user activities, application usage, and connectivity status.
Why Secuvy?
Unmatched Integration Capabilities
Innovative Technology
Proven Expertise
Scalable Solutions
Commitment to Excellence
Experience Secuvy in Action
See How Our Solutions Can Transform Your Access Intelligence
Awards
Additional Resources

What inspired the rise of LLMs and why now? We have witnessed the remarkable rise of generative AI, powered by vast amounts of pre-trained data within large language models (LLMs)....

What every privacy & legal team needs to know. Around 2008, storage prices reached a downward inflection point and have been drastically reducing since. Technological advances, such as the rise of SaaS, ...
With organizations storing years of data in multiple databases, governance of sensitive data is a major cause of concern. Data Sprawls are hard to manage and increase an organization’s risk...