Automated Data Subject Access Requests (DSAR)
The Secuvy Platform enables you to comply with global privacy regulations like GDPR and CCPA which mandate businesses to disclose an individual’s personal data upon request, responding within specified DSAR timeframes.
Automate Data Rights Fulfillment
The Secuvy Platform automates DSAR management with dynamic discovery, classification, and user profile linkage. Streamline DSARs, validate deletions, and generate DSAR PDF reports efficiently.
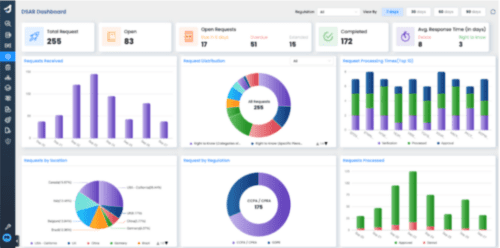
DSAR Dashboard
Secuvy enables you to track all DSARs and provides a real-time view of all the DSAR requests and their status.
Deep Data Sources
The Secuvy Platform instantly discovers, deletes, rectifies, or otherwise actions a requestor’s data across all relevant systems.

Ready to see Secuvy in Action?
Subscribe to our newsletters and get the latest on product updates, special events, and industry news.
